#23 Harvest now, decrypt later (Part II: PRISM)
Hi there! My name is Diego Parrilla. I’m a developer that became an entrepreneur and my latest company is Threatjammer. Subscribe now to my weekly digest about tech, threat Intel, privacy, and security!
You can read the Part I of the article here.
It sounds like a dad’s joke, but one of the first computers the NSA bought from IBM in the 1950s was called “HARVEST.”
The NSA was the first intelligent agency to understand that general-purpose computing would give them a significant advantage in creating and breaking sophisticated cipher codes. This early adoption and the partnership with research universities gave them leadership unmatched by other agencies. NSA and research centers created a perpetual government-academic partnership for developing increasingly powerful computers still valid today. They understood from the beginning that computers evolved very quickly, and they needed to be up to date with all the new designs and system architectures.
Fast forward to the 2010s and 2020s, NSA has become a massive data cruncher of the information that travels through the internet backbones of the world. An organization that can spy on Angela Merkel and more than 35 world leaders. A colossal spying engine.
Edward Snowden -the whistleblower who leaked the US spy program while working for the NSA as a contractor- explained how telecommunications company Verizon handed over all its telephone data to the NSA on an “ongoing daily basis.” He also explained how NSA tapped directly into the servers of nine internet firms, including Meta, Google, Microsoft, and Yahoo, to track online communication in a surveillance program known as PRISM.
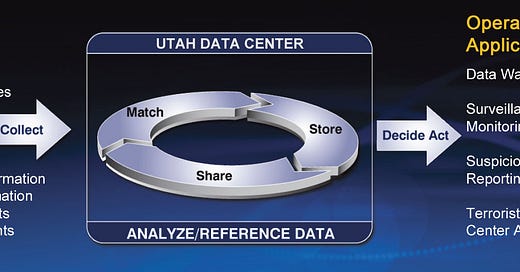
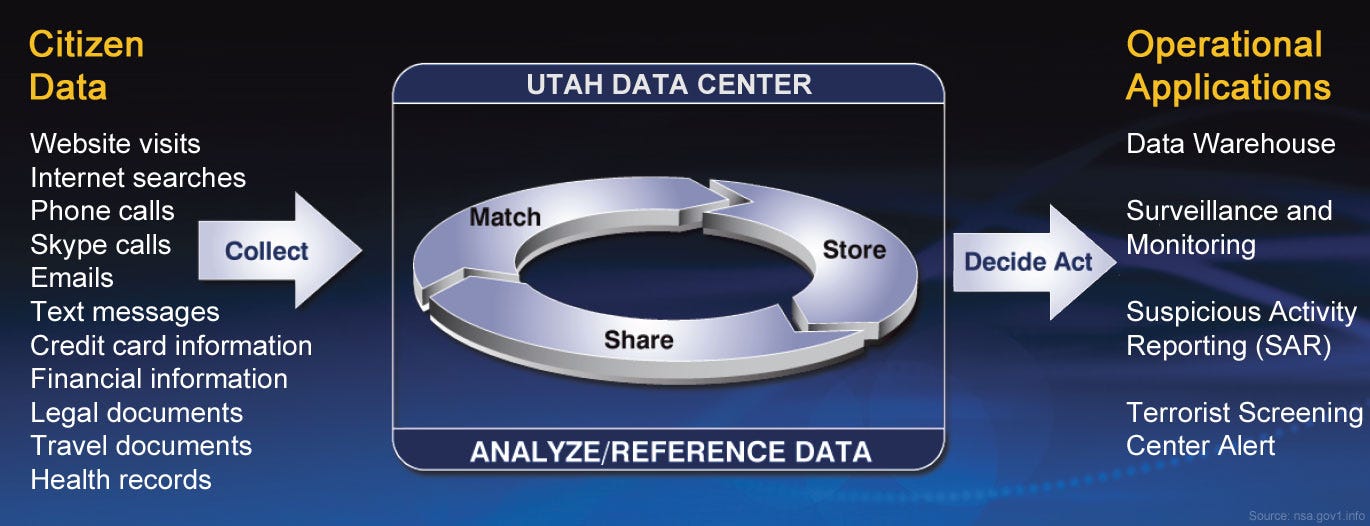
PRISM collects stored internet communications based on demands made to large internet companies to turn over any data that match court-approved search terms. The NSA can use these PRISM requests to target encrypted communications when they travel across the internet backbone, focus on stored data that telecommunication filtering systems discarded earlier, and get data that is easier to handle.
This massive amount of information must be stored in someone’s computer: in the cloud. One of the best customers of Amazon Web Services is US Federal agencies like the FBI and NSA. But the Bumblehive Utah Datacenter is the storage facility for all the data gathered by PRISM and other programs.
The NSA’s data center requires 65 megawatts of electricity per year, and to cool all of that down, more than 7 million cubic meters of water will need to be pumped through the facility daily. The total cost to build the data center was $1.5 Billion. According to Rankred, it’s the 7th largest data center globally.
This massive spying infrastructure is designed to store raw data from multiple sources. Most of the information lay in the cabinets' hard disks for days, months, or years. Until one day, a Person of Interest becomes a target, and somebody decides to retrieve all that data lying in the cooled aisles of the Utah facility and analyze the raw data. And Bingo! You met that person several years ago at a professional event and shared some text messages. The NSA knows it because they could infer a graph of the contacts from the metadata of logs provided by your Telco, and there you were. Then they decided to retrieve your records and sneak around your data to find out if you have something interesting to disclose.
According to NSA, the US's strict legal structures ensure compliance to protect civil liberties, so data is deleted automatically within a set time limit when the legal period is up. What a relief.
The big question is, “what can NSA do with our logged data?” Assuming our communications are encrypted at different levels, it should be hard for them to exfiltrate our conversations. Well, not really. NSA knows what to do to crack our encrypted communications:
The NSA may be the largest employer of cryptologic mathematicians in the United States. There is some evidence of mathematical breaks that are expensive and unlikely to work well against new encryption algorithms, but it’s well-known that algorithms have been cracked due to continuous improvement in computer architectures and/or mathematical flaws.
They try to undermine commercial cryptographic implementations or obtain pre-encryption access to some of the most popular services—direct access to cloud companies or VPN providers to obtain data from their users or implement backdoors.
Steal the keys. Old good sabotage and spying techniques can be cheaper and more effective than a brute force attack on an algorithm. And please, don’t believe the propaganda of good and bad intelligent agencies: they all do it.
So should we give up and let them get our conversations? No way. Some documents revealed that NSA has problems decrypting certain types of traffic like Truecrypt, PGP/GPG, Tor, and ZRTP. These protocols share many cryptographic algorithms: RSA, Diffie-Hellman, AES, etc.
The evidence is that those primitives are still cryptographically strong in 2022 but will be useless if the attack comes from a quantum computer. The case to adopt quantum cryptography is strong based on the information revealed by whistleblowers worldwide: so I want my conversations to be private now and forever. And quantum cryptography matters.
The music snippet
Favorite song of NSA workers for sure.